STRENGTHENING ORGANIZATIONS OF ALL SIZES
BUILDING VALUE AND COMPETITIVE ADVANTAGE
This page was previewed in the Winter 2025 edition of ISE Magazine.
LET’S FACE IT, droning on about impending doom to the organization: “if we don’t deploy resources (money and staff) to reduce our security risks now, then I can’t be held responsible …” goes down like a lead balloon. Whatever you say next is not listened to.
Instead, the executive mind returns to dealing with the issue of the day or how to execute the next big plan. You will notice that the title of this page couldn’t bring itself to use the word cybersecurity! Even at the end of 2025, shockingly and especially for millions of smaller organizations, the “it’s so unlikely, it won’t happen to us” is still prevalent, especially just before they are put out of business!

It’s time to change that with an approach that will open closed minds and positively impact the top and bottom line of the organization.
What's the Breakthrough?
After authoring the article on Resilience in the fall edition of ISE magazine and working on the new resilience guidance with the Cloud Security Alliance, I had one of those “Duh, why didn’t I think of this before?” moments, realizing that it was all in the language and the impact on the listener. It’s switching from the part of the brain that reacts to an amygdala attack to fostering being inspired by new possibilities.
This means that this page is a complete 180o language reversal from almost everything else I’ve been working on including my Cybyr-AI software!
Be assured, it’s not about brain science, it’s about putting all actions in the context of strengthening the organization by changing the mindset to enable new possibilities.
- Creating a structure for low-cost execution with a holistic strategy and incremental actions.
- Executing actions related to avoidance, prevention, detection, and removal of disruptions to the goals.
- Measuring and reporting improvement over time. Then, adapting to the evolving organization and changes that impact the goals for the next iteration.
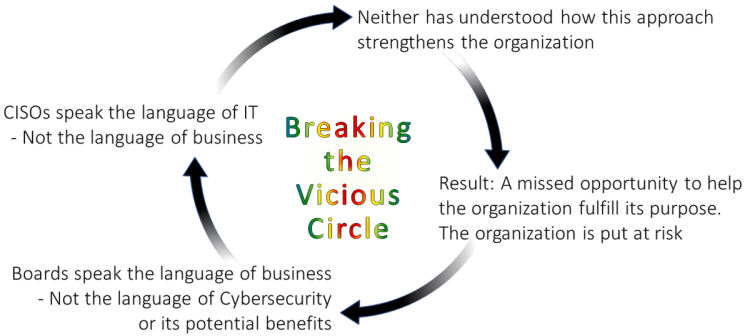
Developing the Executive Language
This begins by using words like “strengthening the organization” and avoiding negative words such as “risk” and “threat avoidance.” I just read a guidance document that used the word “risk” 160 times, along with “vulnerabilities,” insider terms like “security posture,” and acronyms that interrupt the listener’s understanding. No surprises that the board members in the picture above tell such lack or response!
End User Organization Competitive Advantages for Customers
- Build the organization profile so that customers, clients and investors know their interests are being proactively protected.
- If the organization produces software products ensure that R&D uses memory-safe languages and does not rely on unverified elements, especially from open-source code posted on GitHub, etc., make the use of DevSecOps processes as another competitive selling point. This is exactly the strategy put forward by CISA recommending that companies self-attest the diligence of their processes help keep their customers safe.
- Supply Chain security is no longer blindly taking products and trusting they are safe. Ensure that any supplier verifies and takes full responsibility for the products or services they provide.
- If you sell services or software products, examine how well-documented the resilience and security procedures support sales to differentiate from competitors, remove supply chain fears, etc.
- Just like privacy policies that no one reads, the security policy should be posted to identify the organization as a modern, powerful company.
- The same applies to obtaining insurance at lower rates, meeting legal and SEC requirements, and defending its reputation if supply chain vendors cause problems.
Service Providers: Two Killer Advantages to Offer Customer/Clients
The focus here are two difference-making strategic services that could be unique and compelling client offerings for service providers.
- Offering the Zero Trust security services covered in my Assume Breach page and article means providers can potentially eliminate ransomware for their customers by detecting and nullifying ransomware attacks that have breached an organization’s access systems and networks. Specifically detecting the discovery of lateral movement and elevation of privilege seen in almost all Ransomware as a Service Advanced Persistent Threat attacks. This is exactly the kind of thinking that differentiates Tier 1,2 or MSSP offerings to customers large and small.
- The next is an ambitious service when all security services are delegated to service and or cloud providers to outsource all security functions to service providers especially those providers delivering Network as a Service which allows users to choose network services subscriptions based on cost and security functions across a wide variety of locations and disciplines.
Creating a Holistic Strategy and Incremental Plan
A Holistic Resilience and Security Policy covering the scope of actions and the goals measuring the impact on the organization. Holistic here means every department and line of business, collaboration with all supply chains, including outsourcing, evolving over time.
- The Plan of Action. This lists short-term actions to be undertaken by each department under your guidance. The execution of the plan will be either action completion or achieving measurable milestones. Its scope includes sales and marketing actions, legal, conformance and compliance, HR, etc., that strengthens the organization. The point is, of course, not to get overwhelmed by too many tasks at once and to observe measurable progress.
- Much of this work will consist of interrogation of the organization’s departments to discover vulnerabilities and make agreed recommendations. This is one of the reasons that I wrote Cybyr-AI, my Expert Proactive AI Software to personalize and automate the process, make recommendations, and measure results.
However, you may choose to do this yourself (external cost = 0) or with help from a consultant (like me!).
Executing the Actions in the Plan
This section breaks down the main tasks related to avoidance, prevention, detection, and removal of disruptions to the goals. The good news is that with one exception, they are zero cost, or are already in standard product offerings currently in use.
Avoidance and Protection
Here are some basic actions to take and not to take.
Phishing is easily the #1 source of attacks. There are at least 10 types. However, don’t waste resources on anti-phishing training courses. Recent studies from MIT, etc., show that training is 95% ineffective/useless. Here’s my cutout and avoidance “device” to stick on your monitor or screen …
Cost = Zero
You likely know all these, but maybe you don’t: Zero access to corporate networks from unapproved devices. Approved devices must be automatically updated, containing approved software. User authentication (low cost) must only permit access at approved times for approved transactions from approved locations. Executives— that means you too.
Always use passkeys or multi-factor log ins to approve applications. Never reuse an ID/ password or allow people to log in with Google or Facebook identities. If you do, and one site is compromised, as thousands have, then every one of your sites is compromised.
Cost = Zero
Detection and Removal
In terms of protection of assets to avoid ransomware, I covered this on the Assume Breach page and the Resilience page and article covered asset protection and the automation of asset updates in detail.
The good news is that there are several low-cost options available. For users of Microsoft Office, the email phishing detection is constantly being updated. Anti-malware software from Microsoft Defender, McAfee, Malwarebytes, etc., is likely already in place.
Cost = Relatively Small
Software Tsunami Warning
I cover around one hundred types of security software and packaged solutions on my cybyr.com/cyberpedia page. The actual number of security products is in the 6-10,000 range! However, the only type of software I think is beneficial for the end-user is Endpoint Detection and Removal software.
Ongoing Measurement Reporting and Adaptation
In terms of measuring progress, this is where I have spent much time on software that both measures your status, prioritizes recommendations on next actions and tracks improvements. Finally, as each cycle of execution completes, it’s time to adapt to developments in the organization and prevailing circumstances, ready for the next cycle.
Financing: Resilience and Strengthening as a Profit Center
Resilience and Cybersecurity can be costly if not carefully implemented. However, they have become a competitive necessity.
The recommendation is to calculate the number of customers who will only do business with organizations who have comprehensive and well-documented cybersecurity procedures. Multiply by the revenue generated from them. The second part of the equation is to divide the cost of the actions by the number of customers to see the net positive impact to profitability per customer/client. This can also be leveraged as a competitive sales and marketing advantage to create additional business revenue. As resilience evolves, the impact becomes measurable and feeds back into the decisions on threat appetite when deciding what new actions are affordable (or not).
Priorities
"If you can't measure it, you can't manage it."
This is the beginning of some detailed analysis. It touches on some of the much more complex considerations to be found in our Cybyr-AI software:
- No executive understanding of the risk to the organization typified by “it won’t happen to us” “It’s an IT problem” and “we are too small to be targets.” No understanding of who the “enemy is,” Executive responsibility is abdicated to IT, not delegated” Result: Strength Factor when addressed 30..
- No understanding of the positive competitive positioning that comes from a robust secure organization. Cybersecurity is viewed as a negative and receives little attention or role in success. Strength Factor when addressed 10.
- Lack of security policy and implementation plan or restricted to resilience. No sense of a journey for the whole organization. No access control policy. No recruitment policy. Strength Factor when addressed 15.
- No holistic approach. I.e., every department has accountability, with tasks and actions to minimize vulnerabilities. Strength Factor when addressed 20.
- No supply chain policies, and standards for choosing suppliers to use best practices and their own security polices for what they supply as products and services. This includes outsourced CPAs, financial advisors and recruiters and web hosting companies, software plugins to WordPress, PR companies not forgetting software and security vendors. Strength Factor when addressed 20.
- Everything else from anti-phishing, anti-malware software, threat detection, human error avoidance via automatic software updating and Zero trust implementation, no BYOD policy, etc. Strength Factor when addressed 5.
Resilience and cybersecurity live in the world of “you are only as strong as your weakest link.” Therefore, the above are a just few examples of the relatively important actions to be taken to strengthen the most dangerous vulnerabilities. Much more on this as the page develops.
Summary
I hope this structured approach gives you some inspiration for a more engaged organization at limited external expense. Yes, cybersecurity is critical but the overarching context is the strength of the organization. If nothing else, it will get the executives thinking positively raising their interest and awareness. The reaction will hopefully be more as in the picture below than the one at the top of this page!


