DELEGATING RESPONSIBILITY WITHOUT ABDICATION
Creating Compliance and Organizational Protection

If the principle of Zero Trust “Never Trust, Always and Continually Verify” is to be followed, then how do you verify external organizations, their products and services that are not under your control?
The answer is that it’s practically impossible know how their company operates, or the services and software they deliver are developed and deployed, leaving you with unknown vulnerabilities for which you still remain responsible.
Zero Trust
 This page is based on the article published Aug 2nd 2023. Click here. It has been much refined here and has grown in November 2023 to include the impact on Network as a Service.
This page is based on the article published Aug 2nd 2023. Click here. It has been much refined here and has grown in November 2023 to include the impact on Network as a Service. Transformational Cybersecurity - Zero Trust Thinking
For me, “transformation” has a specific meaning. It’s the indication of a moment of discovery that inspires and immediately creates a new way of thinking—a new future. My intention is that this page creates such a moment for you one that’s not just informative and not just more hype.
Multiple connected clouds, edge compute, the explosion of IoT deployment, supply chains and distributed workforces have created the cybersecurity monster. It’s able to attack a myriad of vulnerabilities. The days of the data center’s single defendable perimeter are long gone. It’s been a few years since John Kindervag’s Zero Trust mantras of “Assume Breach” and “Never Trust, Always Verify” became the imperative – the essential and now only viable way of ensuring that the network cloud ecosystem or Network as a Service is secure.
That’s why this page deals with the conundrum of delegation to third parties that you don’t control – guiding them to be liable for what they claim about their services and products all without abdicating your own responsibility.
Applying Zero Trust Transformative Thinking
Zero Trust’s “Never Trust, Always Verify” thinking, should not only be applied to your operational network, but everywhere! You may begin by wondering about the services and software, database systems, applications and network devices. “Why should I trust them now?” What about the companies that create the products? How do I know that I can trust them? Are they using best practices suggested by this year’s White House Security Strategy? How can I trust the code or the APIs they are using?
These are all the right questions. The answer is you don’t need to trust them – but you do need to hold them accountable!
This is critically important, as we saw in May’s attack in Dallas, it applies especially to the security software and the supplying companies which the Royal Ransomware attack disabled.
A Blueprint for Risk Reduction
If this sounds hard it isn’t. In fact, here are several best practices—effectively a Blueprint for Risk Reduction to bring order to the complexity of cybersecurity. In order to protect user organizations, implementation of Zero Trust enabled services and products, they must be in compliance with the following protective measures applicable to their organization, product development and operation. Such compliance should be made available transparently to subscribers of such products and services.
"Trickle-Up" Benefits for the Board
By “trickle-up” we mean that this methodology provides much needed (if not much-understood or realized) company “protection-of-responsibility” for the executives of the company and in turn, shareholders, staff and customer clients. Maybe this is the most important information that a CISO could communicate upwards. Obtaining written verification of supply chain services and software self-attestation that is properly documented it’s like gold dust. When used for cybersecurity insurance and documented along with privacy notices, the risks from third party causes may not be eliminated but at least accountability can be delegated. When we say supply chain we include all subcontractor organizations, physical security companies, web CMS, CRM software systems, CPAs, recruitment companies and anyone with access to sensitive information. Yes, all other security best practices need to be deployed but those at least are under direct corporate control!
Taking Actions to Empower Your Organization
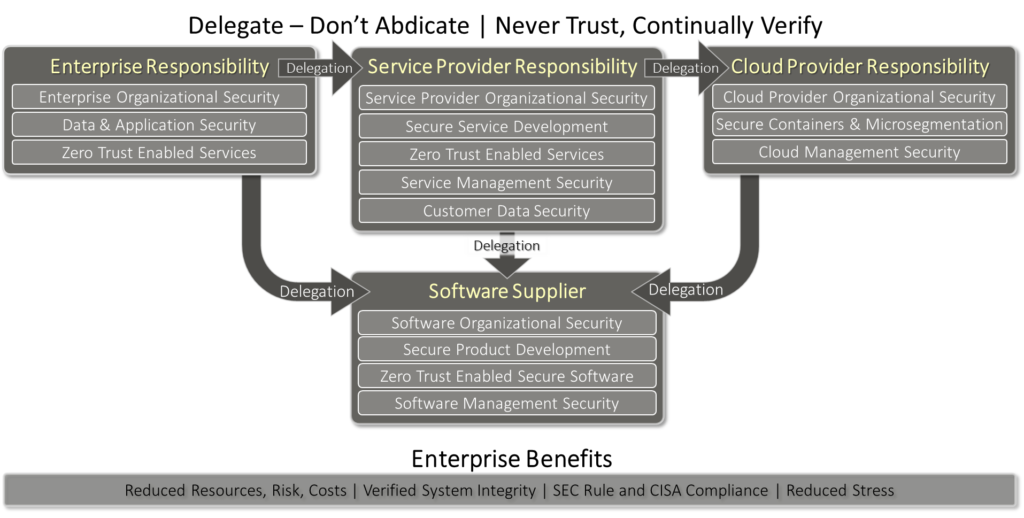
The good news is that this thinking enables empowering actions to be performed. The 26 questions in the Figures below are examples from my Holistic Cybersecurity as a Service offering. It’s the categories that are important. The CISA initiative on “self-attestation” of software companies is a great start, going in to more details on the Development section below. It will remain to be seen what goes into the final version scheduled in 2024. The CISA coverage does not get into the organizational nor operational aspects of software. This is a serious omission since it leaves many areas more areas of vulnerability. There are 6 parts to delegation:
- Organization – how the supplying organization itself follows holistic cybersecurity best practices, covered elsewhere on this site.
- Product and or Service Secure Development, marketing and maintenance via DevSecOps.
- Product or Service Functional Operation. Does it operate securely and implement Zero Trust principles?
- Management Resilience to disabling attacks, DDoS, unauthorized management access.
- Delegation to any and all third party software and service providers. Recursively applying the above points to its supply chain. I.e. service companies must create the same validation their software suppliers.
- Finally, this verification should be monitored for changes. suppliers should ideally re-verify their submission (say) quarterly.
Yes, three more because the operational aspect of a software product has two aspects, covering how it operates AND how it’s managed. An example is a Firewall implementation whose functions can be disabled by a denial of service attack via its management ports while it’s busy filtering packets. The ones about an organization will be similar but will vary by product type. This section updated has been after the article was published.
1. Holistic Organizational Best Practices
(Applies to contracted service providers, direct and indirect software suppliers. It also applies to an enterprise’s own organization where delegation is straightforward.)
| 1. | Executive-level Security Policy and Strategy. |
| 2. | Curated and automatically updated software, device drivers, data, and networking assets. |
| 3. | Insider threats and social engineering strategy. |
| 4. | An implemented policy for multi-factor authentication, passkeys, trustworthy password managers, least privilege, etc. |
| 5. | Proactive phishing attack, lateral movement and elevation of privilege malware, intrusion, threat detection and prevention software etc. |
| 6 | Use of “Bring your Own Devices” is disallowed everywhere, including subcontractors. |
| 7. | All third party software is similarly screened for vulnerabilities, e.g., CMS, CRM, and databases. |
2. Development Best Practices
(Applies to contracted service providers, direct and indirect software suppliers)
| 1. | Development, Security and Operations(DevSecOps) includes automation of monitoring and built in event notification. During 2024 it is anticipated that some of this section will be addressed by CISA’s requirements for software organizations to provide self-attestation of their DevSecOps practices. |
| 2. | All software is encoded in memory-safe languages, e.g., Rust or C#. |
| 3 | All third party code is verified malware free, especially any open source code. |
| 4 | There is a proper Software Bill of Materials in place. |
| 5. | Software/updates are regression-tested for protection to threats in section on the right and all hardware, software, drivers, and firmware updates are automated. |
3. Product & Service Operations Best Practices
(Applies to contracted services and any of their subcontractors.
Applies to direct and indirect software deployed.)
| 1. | Database software/apps only permit bulk encryption, exfiltration of data via authenticated privilege. Each application’s data is organized using microsegementation techniques. This applies to provider and specifically to the protection of a service providers’ customer databas of enterprise customer data and information. |
| 2. | All data or software defining the privilege levels of users’ software and devices are protected/ encrypted to protect against elevation of privilege attacks. Privilege includes length or time, amounts of data to be accessed, written or read, including software updates, approved encryption types. |
| 3. | Access control and identity management software is similarly verified and protected. |
| 4. | Detection, notification, and prevention of any attacks is via automated monitoring. |
| 5. | Multi-factor authentication is applied to critical software and databases not just users. |
| 6. | All APIs are certified to mTLS, SAML OAuth2.0 specifications. |
| 7. | Detection and prevention are implemented for lateral movement attacks, drive-by, man-in-the- middle, side channel, TCP split handshake attacks, etc. |
4. Product & Service Management Best Practices
(Applies to the management of services and software deployed.)
| 1. | All data or software defining identity, access control list, the privilege levels of admin users and software are protected/encrypted to protect against elevation of privilege attacks. Privilege policy includes time of day, types of management data to be accessed, written or read, including software updates, approved encryption types. Access control and identity management software is similarly verified and protected. |
| 2. | All firmware or device updates are only from certified sources. |
| 3. | Management software detects and protects unauthorized out-of-policy access, disabling denial of service attacks with service suspension if encountered. |
| 4. | Detection, notification, and prevention of any attacks is via automated monitoring. |
| 5 | Multi-factor authentication is applied to critical management software not just users. |
| 6. | All APIs are certified to mTLS, SAML OAuth2.0 specifications. |
| 7. | Detection and prevention are implemented for Distributed Denial of Service, attacks, lateral movement attacks, man-in-the- middle, side channel, TCP split handshake attacks, etc. |
5. Delegation v. Abdication and Liability
- Software and service companies that cannot give satisfactory answers to the majority of these questions – in writing – are essentially “disqualified.” The scary part is that they maybe haven’t thought about them! You should not contract with them and subscribe elsewhere. In any event, your contracts/legal department should have a say. I do believe that by asking these questions you will create an important partnership with your suppliers and help them establish their own best practices to align with the 2023 US Cybersecurity Strategy (see section 5.3). This is also exactly aligned to the June 2023 update from the White House on the Secure Software Development Framework initiative, where companies are being required to we said, this shift in thinking is effectively attest to their development practices.
- Conversely, end user organizations who do not ask these questions of their software suppliers, service providers, their security vendors and of their own departments are likely abdicating responsibility and will remain liable or vulnerable or worse.
For me, this is the transformative moment that I referred to earlier. To truly delegate not abdicate, to take control to be responsible. Now, you’ll no longer be overwhelmed by this topic.
As we said, this shift in thinking is effectively a Blueprint for Risk Reduction that empowers your actions and your role!
Applying Delegation to Network as a Service
The development of Network as a Service and its goal of on-demand, subscription-based services also requires simplified choices for consumption of these services. It provides the opportunity for “properly” delegating network security to providers and their software suppliers saving large amounts of costly enterprise resources and implementation time. The following was first presented in October 2023 at the ONUG Fall event. This simplified approach to security could also be applied to a plethora of other services but the methodology would need to be replicated for each type – hence the advantage of Network as a Service.
Keep Up Your Awareness
There are new threats developing each day. Many are multifaceted, complex, and polymorphic. “Hacking as a Service” toolkit is one ugly example of why you need to keep alert. One of many credible resources is cybyr.com. There, I’ve introduced Security as a Service with software that walks you through the process and measures your progress holistically, over time. Become a passionate student, visit my “Cyberpedia” page explaining 270+ cybersecurity terms – many used here—and for the latest breaking news on threat detection and prevention.
