Cybyr.com: Every Organization Protected

Welcome to the the home of Holistic Cybersecurity.
We provide services and software for your entire ecosystem – not just IT, measurably strengthening your resilience and avoiding mistakes still made by the largest organizations.
Keeping you aware of the latest in the complex world of Cybersecurity, AI and Networking.
Our purpose is that every organization is protected from cyber-attacks
LATEST NEWS, VIEWS, SERVICES & FEATURES
Breaking
Cybersecurity News - March 2026
Top Stories
Middle East War Brings Challenges
A New Era: AI-Generated Malware
OpenClaw Chaos
NewArticle - Dec. 2025
Stengthening the Organization
Leveraging Cybersecurity as a Business Advantage expressed in the language of the executive team.
A New Type of AI Software
Blends Human Expertise with AI
Transformative: Asks You Questions, Makes Recommendations, Tracks Risk Reduction, Organizational Strength
Informative: Integrates expertise and GenAI with automated updates from the world of cybersecurity.
Secure, Acts as Trusted Advisor, Current, Integrated with our VCSO Service
Game-Changing
Ransomware Prevention
A new approach to Ransomware Prevention that Assumes a Breach has already occured!
CYBERSECURITY KNOWLEDGE BASE
CyberPedia Intelligence
More than the most comprehensive and up-to-date glossary of terms . . .
Our CyberPedia Page looks beyond the vested interest and bias to dissect the very latest
cybersecurity terms and ideas. Click here to access. Updated February 2026.
- 430+ descriptions and explanations of cybersecurity and AI terms
- 125+ threat types | 70 Defensive tool types | 30 packaged solution types
- 150 + acronyms | 16 Zero Trust terms | 21 AI related definitions
- Insider perspective separates actual functions from marketing hype
Our Cybyr-AI software Knowledge Base provides access to the latest news, blogs videos special in depth discussions on key cybersecurity topics.
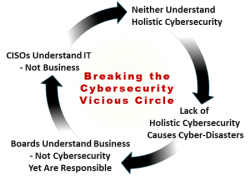
An Introduction to Holistic Cybersecurity
Most Cybersecurity services and products focus on Information Technology, selling branded solutions, missing critical actions. They miss the impact on the entire organization, leaving weak links to be exploited. If it enables you to mitigate the most vulnerable threats to your organization’s existence, then this work will have succeeded.
I wrote this for those executives who have neither the time nor inclination to read it! If it’s not understood or adopted by the organization’s leadership, the organization will lose the cybersecurity war and will likely fail. This new Holistic Approach To Cybersecurity covers all aspects of your organization, large & small, starting with the Exec team plus your suppliers and contractors.
Holisitic Cybersecurity - A Deep Dive
The in-depth What, Why, How and How of Holistic Cybersecurity, developed from my article first published in ISE magazine in April 2024. Click here.
Work on holistic cybersecurity began in 2018, followed by the publication of my book: “Hey, Who Left the Back Door Open?” The strength of the front door doesn’t matter if the back door is left open. Oh, and in today’s Cloud-oriented world, there are no walls, let alone a back door to defend – and anyway, the enemy is likely already inside!
More Cybyr.com Features and Resources
Feature
Network as a Service Innovation
Bringing Enterprise Advantages
Comparing & combining SASE, SSE and NaaS to turn secure networking upside-down. Click here for a major 3-part feature.
Cybersecurity for SMBs
Cybersafety without the Cost
Now Every Organization
Can Have Cyber Safety
A New Methodology & Virtual CSO service for those with no budget, resources or expertise. Measurably reduce risk by implementing 60+ recommendations.
Reducing Supply Chain Risk
Our breakthrough on verifying suppliers of services, software, security solutions and other suppliers to avoid the dangers of abdicating responsibility.
If only the world’s largest organizations had adopted this.
Feature
Network as a Service Innovation
Bringing Enterprise Advantages
Comparing & combining SASE, SSE and NaaS to turn secure networking upside-down. Click here for a major 3-part feature.