CRITICAL INFRASTRUCTURE
Exploring New Networking and Cybersecurity Strategies


This page is based on the article published December 2023. Click here. This page will continue to be developed to include new choices as they mature.
The definitions of Critical Infrastructures covered by the U.S. Government’s Cybersecurity Infrastructure and Security Agency (CISA), reveal the mind-bending breadth of its scope. What distinguishes the categories defined is the impact on wide areas of the population or on specific communities, “… should any of these infrastructures be incapacitated or destroyed.”
This page examines how evolving and related networking, security and business models create challenges and decisions for specific critical infrastructures. Instead of attempting to boil this ocean we address three important areas common to implementors and operators. They are:
- Network ecosystem evolution – Network as a Service
- Operational network business and security
- Security – the basics that are still constantly ignored leading to high profile incidents
The Context: Distinguishing Critical Infrastructures
Looking at CISA’s list below, you will see why it‘s beyond this page’s scope to go into detail of any of the 16 sectors or 70+ interrelated sub- sectors served more than 80% by non-government organizations. These are covered in detail on the CISA site.
We have split the list into two groups. The first being where the effect is immediate and rapid response is most critical. The second group has less immediate impact but is also critical.
All are costly undertakings but what distinguishes the first group is that disablement is so much more impactful than even business cost. Making such infrastructures resilient to incapacitation encompasses architectural choices, holistic approaches, threat avoidance, prevention, and automated recovery. Some areas such as “smart cities” pharma companies are not covered but are also critical. The Dallas municipality cyberattack impacting the whole community comes to mind. Those relying on IoT/IIoT devices requiring phys- ical device security are especially vulnerable and open to human error.
Caution is required when looking at approaches based on thinking that predates Cloud proliferation, modern IoT systems, distributed workforces, connected supply chains, current network infrastructures, COVID-19 and state-sponsored cyberattack.
| CISA-Defined Sectors | Sub-Sectors Where Very Fast Response Is Required to Protect Life Include |
| Dams | Management, water retention, control, and energy conversion systems, etc. |
| Defense | Location infrastructure systems, communications systems |
| Emergency services | Law enforcement, fire, rescue, emergency medical services |
| Energy | Electrical generation, grid systems, oil refineries, pipelines, natural gas, wind, solar |
| Healthcare, public health | Hospitals, epidemic prevention & treatment, etc. |
| Nuclear sector | Active, test reactors, medical products & waste management |
| Transportation systems | ighways & traffic management, road delivery & hazardous material transport; rail passenger, freight networks, stations |
| Water and wastewater | Capture, purification, storage, distribution of water & wastewater |
| CISA-Defined Sectors | Supporting Infrastructure |
| Communications | Undersea, satellite & terrestrial, dedicated & Internet networks. 5G, fiber, microwave & copper, access networks, Wi-Fi |
| Information technology | IT systems, data center, Cloud, edge, applications software, networks |
| CISA-Defined Sectors | Sub-Sectors Where Measured Response Is Required |
| Chemical | Basic, specialty, agricultural, consumer products |
| Commercial facilities | Entertainment, hotels, casinos, lodging, malls, outdoor events |
| Critical manufacturing | Machinery, electrical & transportation equipment |
| Food and agriculture | Farming, food distribution, retail stores |
| Government facilities | Federal, state, local government education, law offices |
| Financial services | Financial management, money storage, transfers |
| Reported Recent Threats by Sector | Reported Critical Infrastructure Events: Q4 2023 onward. Last updated April 2024. |
| CI: General | |
| Commercial facilities: Hotels & Casinos |
|
| Energy: Nuclear sector |
|
| Health Care |
|
| Telecom |
|
| Transport: Aircraft |
|
| Transport: Rail Security |
|
| Transport: Shipping |
|
| Water |
|
Critical Decisions:
Business Needs for Network as a Service
Changes driven by focus on their mission-critical applications are required by enterprises. They no longer have the resources or time to build handcrafted, complex networks.
These requirements include:
- On-demand, services purchased via portals, consumption- based billing without lock-in.
- Seamless access to multi-Cloud workloads and apps located
- Agnostic to infrastructure technologies and providers, performance, and security sensitive.
- Business aware to cope with M&A, policy shifts and
- Integrity of real-time operational networks that serve its
2024 will decide how critical infrastructure organizations will reshape their networks based on how Cloud/Service Providers and Supplier/Integrators respond to these needs.
Enter the new Network as a Service. Services offered will vary to match the capabilities and end user organizational requirements, resources, and capabilities. New forms of Managed Services, Infrastructure as a Service and Platform as a Service will help end users feel secure in delegating to their various partners. It will be essential to always look beyond the marketing jargon to verify that functions offered actually meet your needs without having to pay for service functions that you do not want. This work is being developed within ONUG.net’s NaaS working group.
What will the likely next phase of the network look like?
This shift is shown below but providers & integrators will market their own version. The important thing is the shift that began with data center centric to Cloud and network ecosystem is beginning its journey to a new Network as a Service model. This will be inherently more secure than the everything-to-everything connectivity with almost unlimited attack surfaces. The diagram was inspired by our work in the ONUG Collaborative
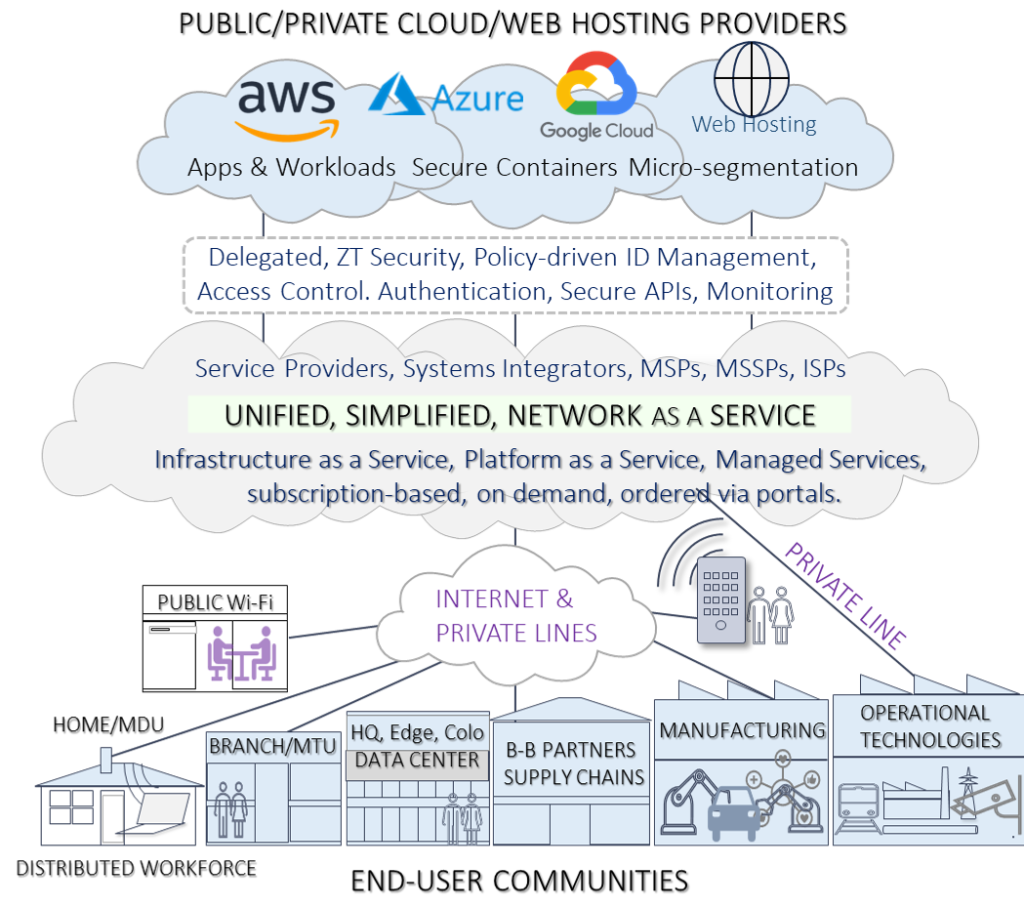
Marrying Business and Network Requirements
These changes will shape how applications and networks are architected and managed, shielding enterprises from the implementations. Three important decisions to be addressed are:
- Will new architectures meet the business drivers with system integrity and save OpEx cost?
- Can this architecture avoid insecure connection to IoT devices via Internet, Cloud-based or other servers beyond the operational networks? Hence the separate connection from OT Networks in the diagram.
- Companies such as Cisco/Splunk, Zscaler, and Verizon will play important roles here, but inspection of the actual functions offered will be important.
Critical Decisions:
Critical Infrastructure Operational Integrity
Some more practical considerations:
As National Transport Safety Board chair Jennifer Homendy said earlier this year of the Ohio rail incident: there is no such thing as accidents and it was 100% preventable. Was this a system and networking failure? Having a trackside generated alarms-only based system not an alert and alarm threshold system with no single point of network failure was a recipe for the disaster that happened. I would hope that after-the-fact other ideas were explored.
Fiber optic networks are expanding, yet the pace of implementation is too slow and the prospect of $60k to $80k per mile fiber installation is daunting. Without commercial viability, critical infrastructure systems cannot function, no matter how severe the impact of their incapacitation.
To address both concerns, adoption of the latest hybrid fiber-copper infrastructure in airport, Smart City, and rail network infrastructures is growing. Fiber/copper can now transmit at fiber speeds, can be instantaneously available as copper is often already in place, provide failover with fiber installations, and provide power for remote monitoring devices. This was addressed in the context of expanding broadband network reach with Actelis in the ISE Magazine article published a year ago. This important trend is of great benefit throughout critical infrastructures.
Cybersecurity Evolution
The migration to Cloud and hybrid models is a two-edge sword, creating new attack surfaces and Internet connectivity. The days of defending the data center as the principal concern of cybersecurity are long gone. Applying the Zero Trust principles of “Never Trust, Always Verify” in the network, for software suppliers and in the organization is a necessity. Thanks to CISA and the SEC, this has become a corporate imperative.
Physical or virtual separation between Information and Operation Technology networks is a big step in the development and protection of your critical infrastructure.
Last but not least, Network as a Service has the potential to reduce the attack surface by harmonizing identity management and authentication. Importantly, it will also lessen the expertise and security work and cost for enterprises—a big advantage. However, it will never remove their overall responsibility to properly delegate to suppliers.
Critical Decisions:
Cybersecurity Best Practices
- Almost every breach or ransomware attack can be traced back
to lack of board oversight, accountability, and lack of understanding
of holistic cybersecurity. That applies to security
software companies too! In fact, if IT-based defense is the only
defense, it ends in tears. The recent high profile MGM Resorts
incident likely had multiple weak links but began with lack of
board imperative and expertise and yes, hotels and casinos are
in the Commercial Facilities category
Basic Critical Actions to Reduce Risk
- Ensure that all these are covered, strengthening weak links, and dramatically reducing risks.
- A holistic cybersecurity approach for whole organization, contractors
and beyond. Have the board implement a security policy and step-by-step strategy to strengthen each weak link. - Curate all critical assets and test resilience. Encrypt all data, network configurations and customer info. Test air-gapped backups in case live data is rendered inoperable or re-encrypted.
- Employ micro-segmentation to separate and protect data. Automate all software updates.
- Access is via multifactor authentication using passkeys rather than usernames/passwords, verified with identity management and with no access from non-company devices.
- Insider threat, social engineering strategies, training and least privilege access must be in place.
- Installed phishing, malware, elevation of privilege, lateral movement prevention is in place.
- Adopt Zero Trust principles of Identity and Authentication, access control, least privilege, automated monitoring including blocking of non-typical user behavior.
- Be cybersecurity threat-aware, map out avoidance and prevention
tasks, automate everywhere. - Know that all software (especially security software) is not trusted but verified using our Verified Delegation Methodology
- Continually assess your security posture, measure progress, take new actions.
- Comply with new SEC rules, with clear documentation
demonstrating your security policy is thorough and implemented.
See the “Security as a Service” page for many more details.
Critical Infrastructure:
Operational Technology Cybersecurity Specifics
- Ensure that the organization’s Security Policy calls out protection of specific OT areas to address.
- Virtually air-gapping of OT from IT networks is challenging since it’s not easy to isloate all outside connections or ensure that externally hosted software is secure..
- Use Zero Trust techniques to create trusted routes.
- Use of packet fragmentation over multiple physical paths.
- Llimiting access to users and software that have insufficient privilege or fail identity and authorization checks to access remote devices.
- Microsoft’s 2023 Security Report found 71% of IoT devices are vulnerable, 46% can’t be patched, and 21% use obsolete operating systems. I.e., total physical or virtual separation of Operational Networks from the Internet is essential.
- The ability to intercept video, traffic sensors are seen in movies but video recordings can also be disabled by techniques that bury malware in H264 encoded video files.
- ASCON lightweight cryptography for IoT devices was selected by the U.S. Government earlier this year. Look for early deployment of implementations now becoming available.
These will supersede the need to use layer 2 encryption protocols such as the IEEE’s MACsec which has had limited uptake.
Address the Top Four OT Threats
- Eliminate external remote access to elements that are part of the same trusted domain.
- Use Zero Trust to limit access to verified, known applications.
- Remove any access to IoT devices via the Internet.
- Properly curate all IoT devices eliminating those cannot be protected, updated or isolated.
| Final Thoughts |
We have addressed a monster topic, with the intention of providing guidance on three critical areas: network evolution choices, operational networks, and overall security. We hope you found it valuable—even if just one or two weak links are strengthened—as you take the next steps in your network and cybersecurity journey to prevent incapacitation of your critical infrastructure network.
Acknowledgements
This work draws from many sources including the U.S. government’s ongoing work by CISA on Critical Infrastructures, lightweight encryption definitions (February 2023), Microsoft’s analysis of IoT vulnerabilities (October 2023) . In 2024 this work has been contributed to The Cloud Security Alliance Zero Trust Working group, to the ONUG.net NaaS and OT projects working groups. It draws upon work from and with with networking company Actelis, from contributors to the Cloud Security Alliance, from countless articles and work on holistic cybersecurity in 2023-2024.
