The world’s only Holistic Cybersecurity as a Service guidance software.
INTENTION
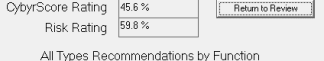
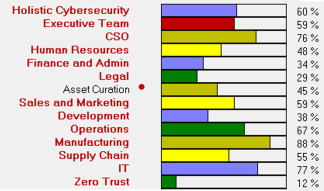
Examine all aspects of the organization & beyond to examine areas to be addressed, recommends specific action, rate current security posture & risk.
Go through each department in turn & through each area of defense from avoidance to detection, prevention & resilience. It addresses from-the-top-policy, awareness, outside supply chains, third parties, organizational & IT issues.
It is self-customized to best fit your organization, enterprises, critical infrastructure, services, etc.
CYBYRSCORE SCOPE
- Security policy – the scope, costs & risk reduction goals as an executive imperative.
- Security strategy – the step-by-step actions & reporting plan to enforce the policy.
- Holistic: Create the cybersecurity baseline for your whole organization & beyond.
- People, HR (including social engineering & insider threats), training (especially anti-phishing), sales & systems, customer service & systems, finance, legal & admin, physical security, marketing & web sites, supply chain, secure development & of course IT.


- Asset curation & resilience, risk assessment.
- Shape & secure your IT/NaaS strategy to minimize your attack surface.
- Implement & testing avoidance/prevention/detection recommendations.
- Elevation of privilege, lateral movement, data loss prevention, advance persistent threats, & security functions, etc.


- Adopt Zero Trust as a state of mind: “Never Trust, Continually Verify.”
- Zero Trust implementation: ID management, authenication, access control, policy enforcement, continuous monitoring.
- Delegate, don’t abdicate to any third party, software company, contractor using the unique Cybyr.com Verified Delegation Methodology.
- As appropriate, address operational networks, IoT, manufacturing, customer interactions.


- Automate everywhere: personal devices, software updates, asset curation.
- Automate network & web sites, people threats, event notifications & testing.
- Measure progress, reduction of risk, regularly report against the strategy.
- Continuously repeat – you are never done.