Zero Trust Thinking - Transforming Cybersecurity
Zero Trust

Page based on the article published
Aug 2nd 2023. Click here and much updated here in October 2023.
When you read “Transforming” in the title above your eyes may have raised to heaven thinking it was more irritating marketing hype. However, for me, “transformation” has a specific meaning. It’s the indication of a moment of discovery that inspires and immediately creates a new way of thinking—a new future. My intention is that this article creates such a moment for you. That it’s not just informative and certainly not just more hype. Yes, it’s informative too, but let’s start at the beginning.
Multiple connected clouds, edge compute, the explosion of IoT deployment, supply chains and distributed workforces have created the cybersecurity monster. It’s able to attack a myriad of vulnerabilities. The days of the data center’s single defendable perimeter are long gone. It’s been a couple of years since John Kindervag’s Zero Trust mantras of “Assume Breach” and “Never Trust, Always Verify” became the imperative – the essential and now only viable way of ensuring that the network cloud ecosystem or Network as a Service is secure.
That’s why this article deals with the conundrum of delegation to third parties that you don’t control – having them be liable for their services and products without abdicating your own responsibility.
Zero Trust Principles
By now, you likely know that Zero Trust is never a complete solution but a strategy and a set of principles. Anyone who tries to tell you that they have a complete solution is either clueless or worse. At best it might be the beginnings of a service that implements and enables some of the Zero Trust principles. What’s critical is to enable critical functions and attributes that implement the principles.
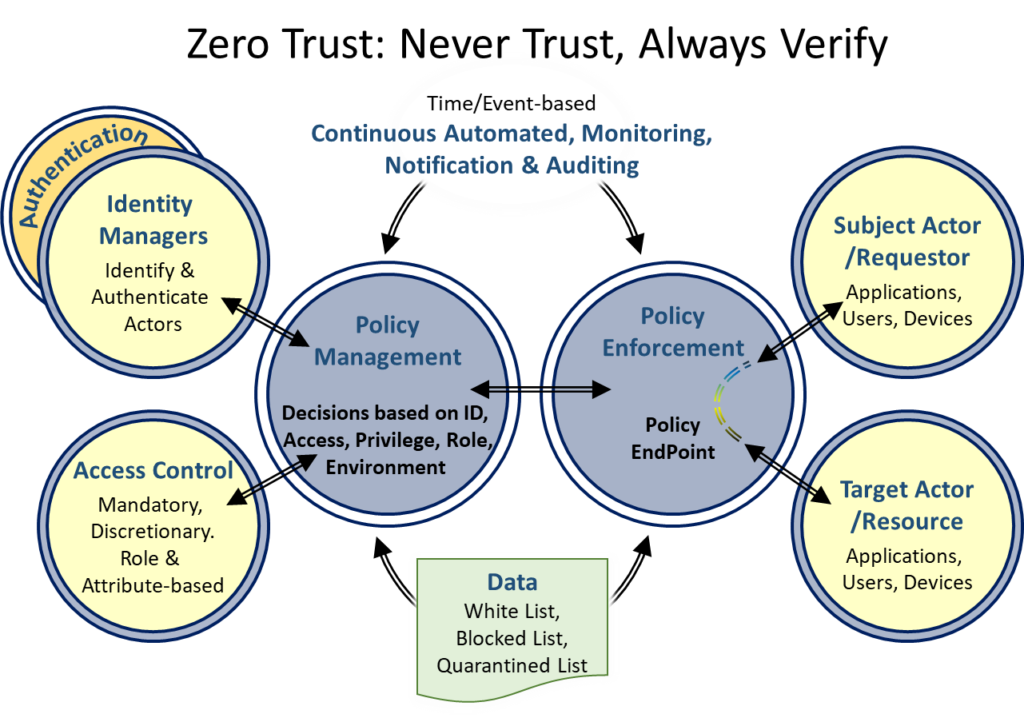
To enable Zero Trust principles, all users, software, and devices must be identified, authenticated, and their access limited according to the role assigned to them. Each actor must only be assigned the least privilege required to accomplish a task. I.e., accessing a limited number of functions or data and only during the assigned
These must be enforced, managed and continually monitored to allow, block or quarantine access and generate notification of such This is evolution from the mantra to “Never Trust, Continuously Verify.” I.e., that inter- changes remain verified ensuring trusted actors do not become threat actors or request out-of-policy actions.
The principles must be applied to all exchanges between micro-segmented workloads, between users and providers, at distributed access points, between IT systems and IoT devices. Its purpose is not just defense against inbound attacks but also preventing exfiltration of critical data.

The Delegation theme has since been fully developed on the site. Click here
