SECURE NETWORK EVOLUTION
Part 3: NaaS Cybersecurity Advantages Challenges & Opportunities
NaaS encourages Common Approaches to Supply Chain Verification
Perhaps the most difficult aspect of cybersecurity are supply chains. Enterprises always retain responsibility but without direct control over suppliers, especially service/cloud providers, their software and hardware suppliers. NaaS brings the opportunity to work with software and hardware providers to have a common approach to self-verification and to strengthen every link in the defensive chain. The scope is shown below, with details on the cybyr.com/delegation page. For example, even the service ordering software should be developed with memory-safe languages, and its management should guard against denial of service attacks, etc.
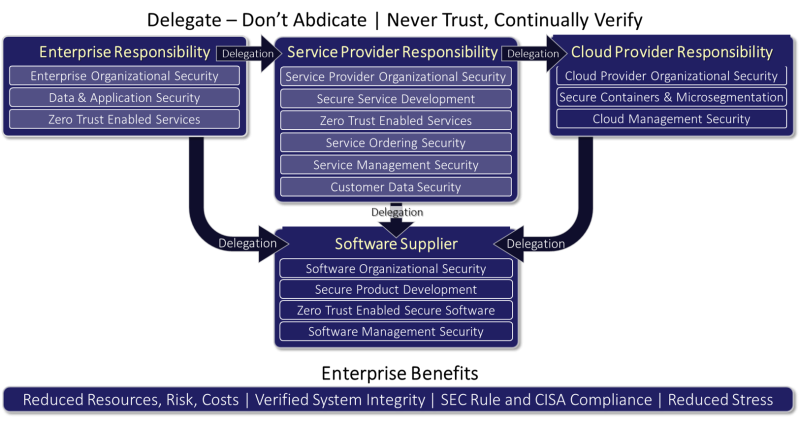
It’s the alignment of service ordering and billing that begin the process and the need to unify service offering without lock-in. Unified single pane monitoring and reporting means that those suppliers that also align their development and management will clearly become market leaders. The natural leaders will be the service providers who will also look to suppliers who can meet the requirements. These best practices naturally develop healthy security habits.
In turn, this will shift the burden from enterprises who typically have had to manage security themselves or risk abdication of responsibility. In turn this will free up expert resources and avoid having to pay for high priced and hands on management of security operations.
NaaS Delegated Security Summary
The power of delegating, while not cannot be perfect, ensures that potential weak links are both identified and strengthened, is profound.
Characteristics and Enterprise Benefits.
- Aligns with CISA self-attestation guidelines and Zero Trust principles to never trust and continuously verify operations
- Provides methodology for enterprises to delegate responsibility to supplies to enable proper accountability and governance.
- Reduces risks, costs and expert resources to oversee network, provider and cloud security and verifies system integrity
- Enables written security policy to meet SEC rules and reduce insurance costs
- Intercepts CISA Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) 2024/2025
Operational Characteristics
- Organizational Security
- Security Policy-driven, social engineering, insider threats, staff training, BYODs banned, MFA/Passkeys, Malware detection & Removal, etc.
- Data & Application Security
- Asset curation, encryption, anti-phishing, least privilege, access,
IdM, MFA, avoidance, prevention - Cloud Microsegmentation, Secure Containers, Workloads, etc.
- OT network separation
- Asset curation, encryption, anti-phishing, least privilege, access,
- Secure Service & Software Development
- Per CISA best practices
- Coded in a memory-safe language
- Zero Trust Enabled Services and software
- Authentication, policy management, enforcement, automated monitoring
- Secure service and software management
SASE, SSE and NaaS - Working Together at Different layers
The following show how SASE/SSE work with NaaS at different layers. Firstly, a generic diagram:
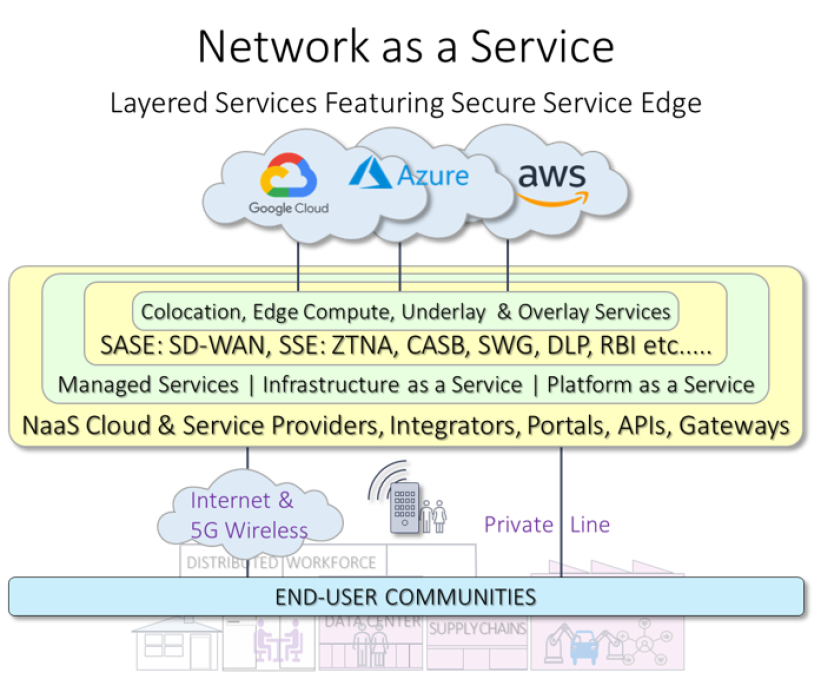
This diagram shows the true flexibility of a well-implemented NaaS system. It shows three providers operating in different geographies. One has implemented SAS/SSE and managed services via Internet access. The second not. The third services a critical infrastructure division operating over private lines to a service provider running an IaaS network. The Managed service provider provides common API services on-demand via a portal or via APIs. Finally, if NaaS is enterprise-oriented, shouldn’t they be at the top of the diagram. It may look a little strange to network people but it does turn the world of networking upside-down!
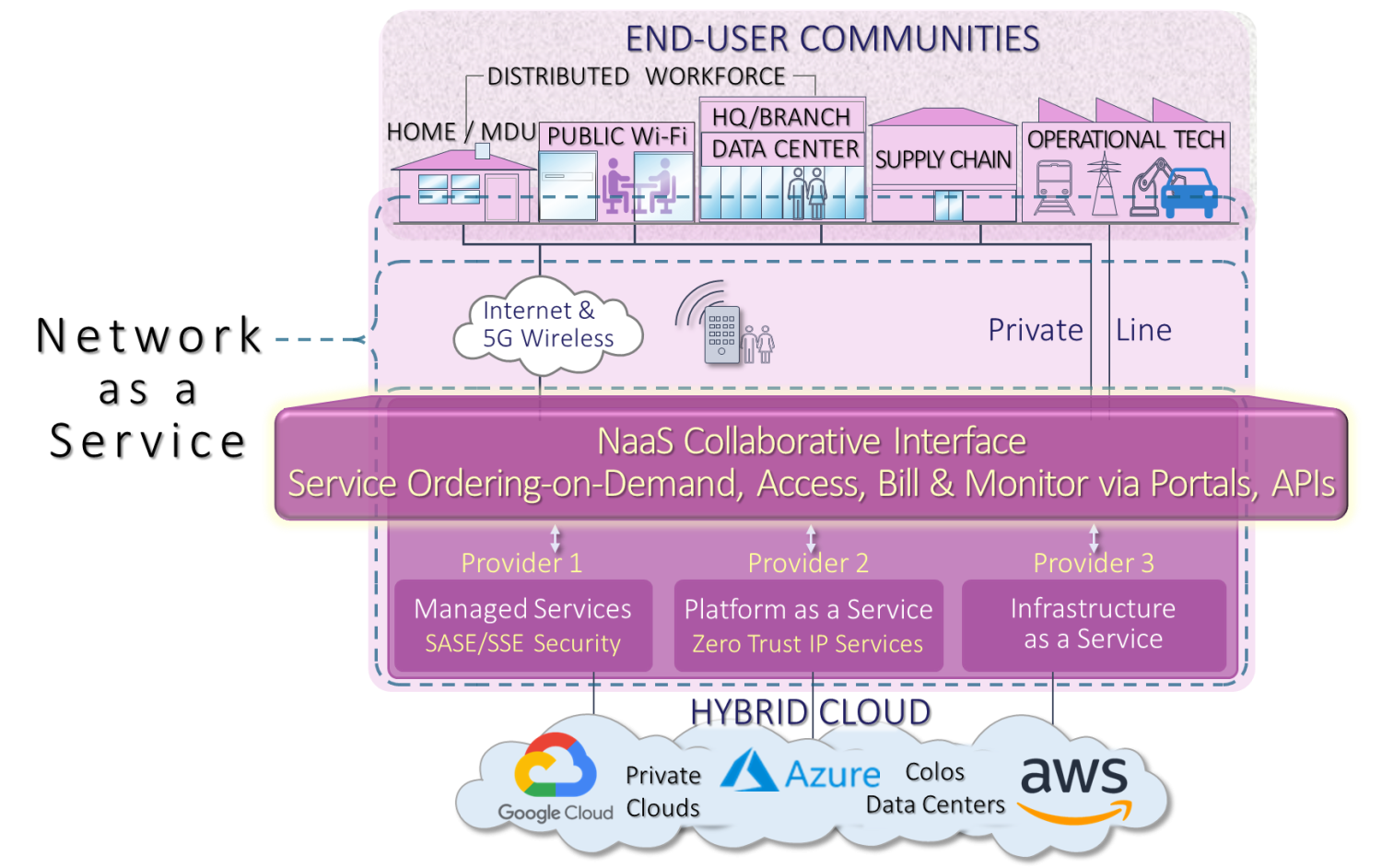
NaaS can be offered in many forms as covered in Part2: Infrastructure as a Service, Platform as a Service. The scope of services can vary too as shown by the dashed lines above. It could be within the enterprise, at the network edge or where several providers are involved, service further into the network. It also shows that the fixed idea of “the Cloud is being replaced by many different combinations of Cloud, Colocation and private edge data centers.
Challenges to Widespread NaaS Adoption
Nework as a Service is definitely an ongoing journey that requires collaboration. One of the first steps is the availability of common ordering and billing portals or APIs. In order to meet the challenges of on-demand services ordered via a common portal, such a portal needs to exist.
One approach would be to allow such a portal itself to be proprietary provided it supports commonly agreed secure APIs. Such a portal would be developed using DevSecOps best practices in alignment with the new CISA recommendations.
This would also allow service provider collaboration since most large organizations span many countries. The same applies to cloud provider collaboration as almost all enterprises wish to connect to applications hosted by multiple cloud providers.
Next, there is the question of network device ownership. Before the era of Cloud-centric and permiterless neworking, Network as a Service was first mooted a decade ago. This was a sticking point. Today’s implementation faces a related challenge that of ownership of equipment that is flexible enough to adapt to dynamic changes v. a subscription model that has a challenging price tag. As we said this is a journey.
Summary
The intention of these three pages was to get through the marketing hype of SASE, SSE and NaaS to reveal the real potential not just for enterprises but for their supplying service providers, software suppliers and keepers of data and workloads. Above all it was to provide both implementation ideas and procurement guidance for what is an exciting next phase of ecosystem development.

